The system dashboard is the view displayed immediately following login to the DEFEND admin console. The dashboard shows:
The operational status of major DEFEND service components
- An overview of general system throughput
An overview of the overall measured risk level across the user pool
- An overview of the number of concurrent users (sessions) currently connected
The status tiles near the top of the dashboard are designed to update you about the operation of your DEFEND service and the ways in which you have configured it to interact with mobile services and email.
Status tiles are shown for:
The continuous authentication engine
Mobile services via SMS or Authy
The database where authentication logs and alerts are stored
The email service used to deliver administrative email such as authentication events
In general, if the continuous authentication engine or database show a status other than "Connected," contact Plurilock for resolution and any relevant outage updates, and operate with awareness that continuous authentication is not currently operating in real time and risk levels may thus be higher than normal across your user pool.
Use the mobile services and email service status tiles to determine whether the configuration details that you have entered for mobile services and email service are correct, and whether the services in question are currently operational.
NOTE
You can see the size of the Plurilock database by hovering the cursor over the information sign on the Database tile.
The charts on the dashboard below the status indicators provide the following information:
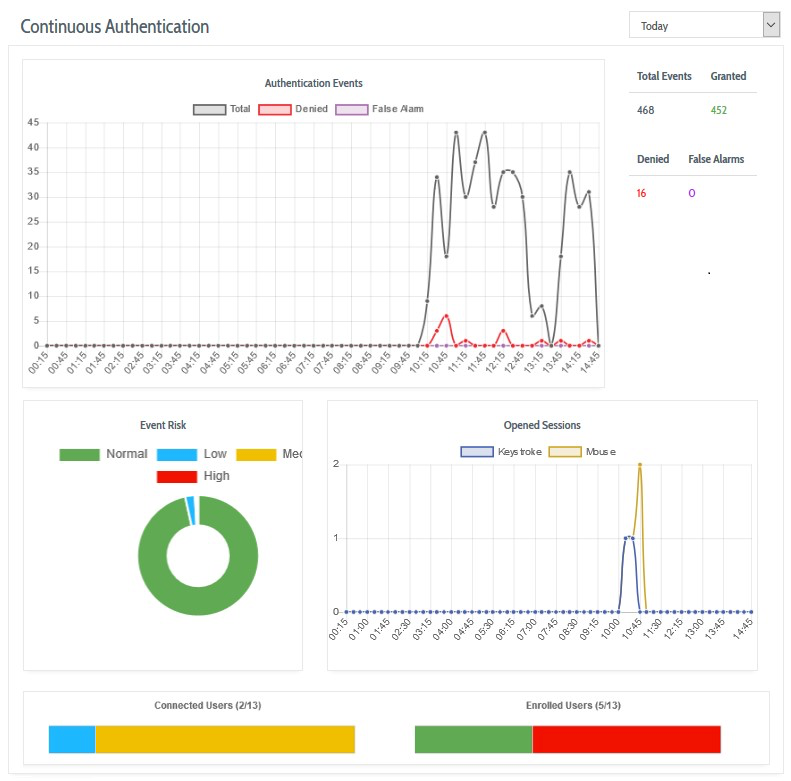
Authentication Events shows the number and type of continuous authentication events processed by the server during the period. The chart displays the total number of events, the number of identity confirmations (‘Granted’), the number of identity rejections (‘Denied’), and the number of decisions that have been marked as false alarms.
Event Risk shows the number of identity rejections events and their assigned risk levels (low, medium, or high).
Opened Sessions shows the number of user sessions, broken down by keystroke and mouse, that have opened during the period.
Connected Users shows how many users are currently online and being continuously authenticated by DEFEND.
Enrolled Users shows how many users are completely enrolled (with both keyboard and mouse master profiles) in relation to the total number of users registered with DEFEND for your organization.
NOTE
The time filters located at the top of each content area restrict the charts data to a specific period. You can configure the time filters to show the results for today, yesterday, last 7 days, and last 30 days. Moreover, each chart also has a content filter. By clicking on the specific type of data, you can exclude this data from the chart.
Table of Contents
- Front Matter
- Trademarks
- Copyrights
- License Conditions
- Disclaimer
- Contact
- Background
- Plurilock DEFEND Platform
- DEFEND Architecture Details
- First Login to the Admin Console
- Creating a Continuous Authentication Site
- Configuring Services
- Configuring Email Service
- Configuring Out-of-band (OOB) Notifications
- Configuring SMS Notifications
- Configuring Authy (Push Notifications)
- Configuring Health Notifications
- Configuring Identity Providers
- Configuring Webhooks
- Webhook Data Format
- Creating and Managing Administration Console Users
- Creating an Administrator Account
- Editing Your Own Admin Account
- Managing Administrator Roles and Permissions
- Continuous Authentication
- Overview
- Deploying Users
- Managing Continuous Authentication Behavior and Enforcement
- Creating and Configuring Groups
- Group Engine and Policy Settings — Application Rules
- Group Engine and Policy Settings — Biometrics
- Group Engine and Policy Settings — Enforcement
- Group Engine and Policy Settings — Data Deletion
- Moving Users Between Groups
- Managing User Biometric Profiles
- Monitoring Alerts
- Using Continuous Authentication Logs
- Understanding Risk Levels and Log Outcomes
- Automated Engine Training
- System Dashboard
- System Audit Logging and Appendices
- Checking the System Log
- APPENDIX 1: Configuring SMS Notification Service
- APPENDIX 2: Configuring Push Notification Service
Was this article helpful?
That’s Great!
Thank you for your feedback
Sorry! We couldn't be helpful
Thank you for your feedback
Feedback sent
We appreciate your effort and will try to fix the article